Compiled by Americans for Innovation Investigators, Latest rev. Aug. 30, 2018

Graphic: KTOO.
If this is your first time to access this timeline or it has been updated since your last visit, it contains
many graphics and photos that must load to your browser. Once downloaded the first time (into your Internet browser's temporary cache files), the site will load more quickly after that. New evidence is added almost daily.
Findings of Fact, Timeline & Database

People you trusted are now
hijacking the Internet
The Greatest Financial Crime in the History of the World
The Theft of the Social Networking Invention
Clear Evidence of Pay-to-Play Public Corruption
Search the entire Americans for Innovation database of actionable intelligence:
Go directly to the Timeline
The following 1990-2018 timeline and supporting facts provide unmistakable evidence of dereliction of duty, fraud, public corruption, the appearance of impropriety, racketeering, monopoly and anti-trust by senior United States government officials, Harvard, Yale and Stanford academics and alumni, judges, law firms and their commercial accomplices. American patent law itself has been hijacked by these individuals and their organizations.
Alternatively, go to an interactive database library for a list and links to all the files, listed by date and alphabetically, at https://www.fbcoverup.com/docs/library/
The American economic engine is being dismantled by deep-pocket intellectual property thieves. They have made the U.S. Patent Office their private toy box.
Constitutional quiz: What are the -only property rights that the Founders considered important enough to actually write into the Constitution?
Answer: patents and copyrights. (U.S. Constitution, Article I, Section 8, Clause 8.) President George Washington himself signed the first patent, U.S. Patent No. X0000001, on July 31, 1790.
The Founders knew the importance of innovation and invention and created the patent system to protect the young republic’s inventors. They believed patents would grow the economy with new ideas that create new jobs and wealth. But without patent protection, inventors and their investors have no incentive to risk their time and treasure to do the hard work of inventing.
Leader Technologies of Columbus, Ohio, risked 145,000 man-hours over five years with an investment of over $10 million to invent the platform that enables social networking. Leader legally filed for patents that they believed would protect their invention.
But a pattern of public-private corruption—as shown in the following timeline—allowed the well-financed vendor of social networking to steal Leader’s invention, reproduce the design, and then use their ill-gotten gains to perpetuate their crime. They excused their theft by falsely asserting that the technology system was "open source" (i.e., "free") software.
What inventor wants to spend years perfecting and patenting an invention that may then be stolen with impunity? What investor will trust his investment to a government that will not protect the entrepreneurial risk?
When inventors are not rewarded for their inventions, society suffers. China, once known for inventions like paper and fireworks, is now notorious for industrial espionage and intellectual property theft and for copying rather than innovating.
Do we want to risk becoming another China?
To foster the inventive spirit that made America the world’s innovator, we must protect and reward our inventors, and address the corruption that has allowed companies like Leader Technologies, the true inventors of social networking, to be fleeced by the system that was supposed to protect them.
The Greatest Financial Crime in History:
Theft of the social networking invention
Brief summary of the MANY smoking guns in this collusion:
| Oct. 11, 1996 |
False Statements Accountability Act—parties can lie to Congress and courts); |
| Nov. 29, 2001 |
IBM forms The Eclipse Foundation |
| Jun. 05, 2002 |
Chandler takes custody of Leader's invention source code |
| Aug. 29, 2002 |
Leader's invention appears in Eclipse version 2.0.1 |
| Aug. 30, 2002 |
Chandler's notes confirm IBM conspiracy to misappropriate Leader's invention |
| Feb. 2-5, 2004 |
IBM EclipseCon 2004, Facebook goes live |
| Apr. 12, 2004 |
Anne-Marie Slaughter proposed A New World Order |
| Dec. 08, 2004 |
IBM"unable to locate" originator of Eclipse code—Leader Technologies |
| Sep. 02, 2008 |
A New World Order to "Fundamentally transform America" |
| Sep. 09, 2008 |
Eclipse boasts 191 members); Dec. 12, 2008 (FISA court gives Eric Holder dictatorial powers |
| Jun. 06, 2009 |
Facebook starts feeding user data to the NSA illegally |
| Jul. 09, 2009 |
Sidney Blumenthal writes Facebook into Hillary CFR speech |
| Aug. 03, 2009 |
Fenwick & West LLP disclosed Leader as prior art on Andreessen social patents, but not on Zuckerberg patents they filed |
| Apr. 2010 |
Zuckerberg refused to provide discovery in Leader v. Facebook |
| Jun. 24, 2010 |
Leonard P. Stark shoehorned into Leader v. Facebook 30 days before trial; and Larry Summers' chief of staff, Marne L. Levine went to work for Facebook on the same day |
| Aug. 10, 2010 |
Leonard P. Stark confirmed as judge, just two weeks after the Leader v. Facebook trial |
| Feb. 17, 2011 |
Obama dines and toasts with Eclipse members in Silicon Valley |
| Jun. 26, 2012 |
State Department promoted Facebook use during public litigation that proved Facebook infringes Leader Technologies' patent on 11 of 11 claims and no prior art |
| Jul. 18, 2012 |
28 Zuckerberg hard drives re-discovered! |
| Jun. 06, 2013 |
Edward Snowden exposed illegal NSA activity |
| Feb. 08, 2015 |
HSBC whistleblower Hervé Falciani exposed Facebook underwriter Deep State |
| Mar. 02, 2015 |
Obama met with Technology CEO Council at White House - All "IBM / NSA The Internet of Things" Deep State members |
| Oct. 10, 2015 |
Obama made mystery trip to Qualcomm |
| Oct. 12, 2015 |
Dell bought EMC - Both Deep State members |
| Dec. 01, 2015 |
Zuckerberg announces $45 billion of fraudulent conveyances |
The summary above is not exhaustive, but merely representative of the massive fraud and racketeering that has occurred and continues to occur.
Bookmark: #new-world
This is the story and timeline of the theft of the invention called "social networking." The thieves are a group we call the "Cartel." and "Deep State." Their motives are ancient. They yearn for money and power. Their goal is a "New World Order." Theft of Columbus, Ohio innovator Leader Technologies' invention enabled them to unify their communications, monitor and control "the masses," and fulfill their rapacious grab for your assets and your liberty.
Bookmark: #Fig-4

Fig. 4—Barack Obama's and George Soros' New World Order is founded on the premise that bold lies are often required to achieve their goal of "fundamental transformation."
The U.S. court-proven facts are that Columbus, Ohio innovator, Michael McKibben, and the company he founded, Leader Technologies, invented social networking in the late 1990’s. Prior to that, McKibben had re-built AT&T’s email system in record time for release with Microsoft’s much ballyhooed Windows 95.
In 6, Leader was awarded its first patent. However, once the Deep State learned about Leader’s invention from an unscrupulous patent attorney and adviser to IBM and the NSA, they wanted it so badly they broke many laws to get it. The invention enabled them to create "The Internet of Things" or "The Internet of Everything" where they could permanently control the digital economy in all its aspects: communications, banking, law, energy, finance, elections, defense, technology, communications, media, healthcare, education, entertainment, politics, guns, food, environment and news.
This sounds like Hollywood fiction, but as you will read in these pages, it is all too real.
The roots of the modern day "One World Order" agenda go back to the 1700’s and philosopher
Emmanuel Kant’s essay. In the 20th century, President Woodrow Wilson’s failed effort to form The League of Nations eventually became The United Nations. The disciples of this soulless, mechanistic agenda include George Soros, Bilderberg Group, the 1910 Jekyll Island Club duck-hunt, World Economic Forum (Davos), Council on Foreign Relations, Wall Street, Silicon Valley, and a slew of politicians, judges and bureaucrats. They benefit personally through investment gains and insider information.
Bookmark: #Fig-5
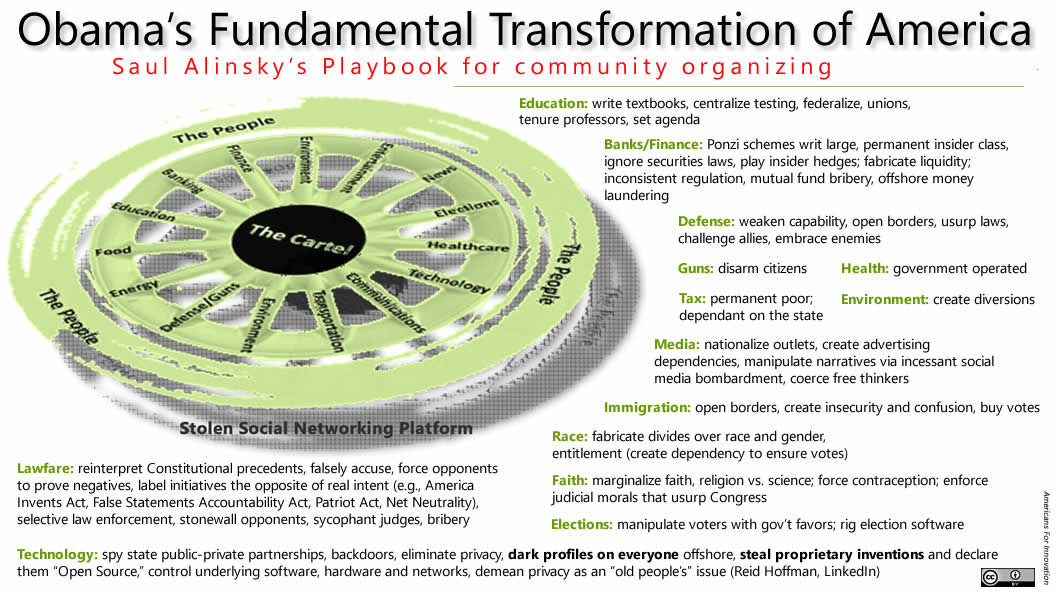
Fig. 5—Barack Obama's "Fundamental Transformation of America" has unashamedly attacked, overtly and by stealth, every major set of moral assumptions that have formed the basis of American society and culture since the founding of the United States.
World government is the notion of a common political authority for all of humanity, yielding a global government and a single state. Such a government could come into existence either through violent and compulsory world domination or through peaceful and voluntary supranational union. In such a world, national constitutions must be subservient to the single state.
Bookmark: #george-soros
Proponents of A New World Order are betting against America

George Soros
On Jan. 05, 2011, new world order godfather and post-WWII Hungarian immigrant to America, George Soros (György Schwartz), stated that the "new world order" will be a healthy, if painful [violent] adjustment." He continued, "China will be the 'engine driving it forward and the U.S. will be actually a drag that is being pulled along through a gradual decline in the dollar.'"[294]
Education or Propaganda? The minds of our youth are targeted
Nowhere is more telling of the Deep State’s agenda than the uproar over Common Core. Critical to the Deep State agenda is the centralized control of education via Common Core in secondary education and M.O.O.C. (Massive Open Online Course) in higher education. Just like the re-education camps of every totalitarian ideology before them (like Mao, Lenin, Pol Pot, Stalin, Hitler, Brownshirts, Komsomol), the Deep State works to control the "narratives" that our children learn.
Where the facts do not fit the Deep State narrative, the facts are ignored or altered. They want to grow obedient, docile, faithless worker bees for their factories. Just like George Orwell envisioned in 1984, gone will be free thinking, free will and individuality. Liberty will be replaced by oligarchies, a permanent under-class, doublespeak, political correctness, disrespect, reading between the lines, hate, intolerance, inequality and brutality.
The digital part of this remaking of education is well down the path. Most secondary schools use Google Docs almost exclusively for their document sharing. In universities, M.O.O.C. curricula are rapidly replacing individualized instruction in favor of the allegedly more "rich" (cleansed and censored) content of "Big Data" and "The Cloud."
Universities are being connected using The Ohio State University's IBM / Microsoft / Oracle / SAP / Eclipse data center as an international M.O.O.C. network hub that Presidential candidate John Kasich approved. The supply of Deep State shiny things to lure educators, parents and students into this morally dark world appears unstoppable as the "users" mainline on the digital drugs.

Anne-Marie Slaughter
This Leader v. Facebook timeline (below) reveals Deep State names, places and illegal acts
Hillary Clinton’s political adviser, Anne-Marie Slaughter (2009-2013) implemented her book—A New World Order (Princeton Press 2004)—when she worked for Hillary at the State Department. She started promoting Facebook at the State Department in 2009, even though Facebook did not have the intellectual property rights. Of note, Slaughter has Hungarian immigrant connections by marriage with Soros, Intel’s Andy Grove and IDG-Accel Partners (China)’s John P. Breyer. Accel is Facebook’s 2nd largest shareholder.
Bookmark: #saul-alinsky
Lying is a Saul D. Alinsky tactic (and also permitted in the Koran when Muslims are dealing with Westerners, Christians and Jews—Qur'an 3:28)
To gain control of the world’s information (and thus its money and power), the Deep State employs the political organizing tactics of Saul D. Alinsky. Hillary Clinton is an expert. She wrote her undergraduate thesis on Alinsky and corresponded with him.[299] Barack Obama employs Alinsky’s bible—12 Rules for Radicals (Random House 1971).
Tellingly, Alinsky dedicated 12 Rules to Lucifer, who he calls the original radical. Lucifer is one of the names for Satan, the Devil, the Evil One and The Dragon (The Book of Revelations 12: 2; 20:2).
The Obamas and Clintons employ Alinksy’s habitual lying technique: Keep the enemy confused and on its heels working to keep up with your lies. Lies also often become truths if repeated incessantly. For example, the lies about Zuckerberg and Facebook in The Social Network movie are accepted as the truth by many.
In the movie and in sworn testimony, Zuckerberg claimed to have invented Facebook in a few weeks, while preparing for finals at Harvard, and drinking. Contrast that with the 145,000 person-hours and over $10 million spent by Leader Technologies. Zuckerberg's assertion is totally illogical, yet it persists.
Obama’s and Hillary’s lies are legion. Their whoppers include: (1) Obama’s oft-repeated promise "If you like your doctor, you can keep your doctor," (2) Obama’s claim to be a Christian to fool voters, (3) Hillary’s fabrication that a video caused the attack on the U. S. Embassy in Benghazi, and (4) Hillary’s ever-changing private email stories which are being investigated by the FBI, with new evidence proving she exposed the highest classifications of intelligence.
They have also brazenly ignored and violated laws. They encourage others to violate U.S. laws themselves, and not respect traditional authority—our borders, the U.S. Constitution and the people responsible for carrying out our laws, such as our police and military personnel. The Justice Department's U.S. Attorneys have become little more than mobsters themselves—A fish rots from the head down.
The Deep State’s corrupt tactics in Leader v. Facebook were purposely confusing in order to discourage the public from learning the truth
The following timeline is complex. That is an Alinsky tactic: Put so many layers of lies on the onion that most people won’t take the time to peel them away.
Americans for Innovation has been peeling away the layers of this Leader v. Facebook judicial corruption onion for years. The Deep State’s onion core is now exposed. Names, places, dates, crimes and motives have been uncovered thanks to the dedicated work of many.
Soros’ New World Order wants to force its will on America and the planet. In their morality, you would be reduced to merely a consuming animal—"a useful idiot" (Alinsky). In their world, faith, hope and love are the antiquated values of weak people. They also have little need for any constitution, law or regulation that stands in their way.
* Alinsky used the phrase "a useful idiot" is sometimes attributed to Vladimir Lenin, although this is in question.
Lure users, young and old, into "The Cloud," then ambush them
Theft of Leader Technologies’ invention of social networking was critical to the Deep State’s plan. With control of the digital essences of our lives ("The Internet of Things" aka "The Cloud"), the Deep State could achieve their new world order more quickly.
Which side are you on?
The moral, philosophical and cultural battle lines are drawn. If we choose the globalist Cartel, the "nanny state" of entitlements will eventually overtake us like it collapsed the Soviet Union. On the other hand, if we choose the timeless values of the U.S. Constitution, we must protect and restore Leader Technologies’ property rights. Then, we empower real, ethical innovators to rebuild our digital networks in a way that takes us to higher ground.
In our increasingly global economy, the U.S. has a major advantage—our inventiveness and entrepreneurial spirit. But we are allowing our advantage to evaporate. If someone had backed up a truck to the "back door" of the U.S. and stolen trillions of dollars worth of property, we would be Carteloutraged and more protective in the future. This is exactly what has happened over the past few years—yet there is no defensive uproar. We cannot allow this thievery to continue.
This restoration of Leader Technologies’ (and others) property rights will expose the decades of corruption that has resulted in this digital takeover. Whether these criminals go to jail, are pardoned or ignored, one thing is for sure-- they must be defunded and disempowered.
Is "the New World Order" too big to fail?
Some ask if social networks are now "too big to fail." The last time Americans thought that was when our too-big-to-fail banks were bailed out in 2008. The taxpayer was stuck with the bill while the bankers continued to pay themselves bonuses. Not a single banker was jailed, fired or even fined. Is this the New World Order we have to look forward to? The answer is yes, unless WE THE PEOPLE put a stop to this profligacy.
These social networks can and will be reconfigured to provide the positive benefits without the abuses of security and privacy. However, they will not be run by the current crop of "public-private" criminals, who must be run out of town, this current President and his cabinet among them.
Read on.
A New World Order is coming. Were you invited to the networking party? (Didn't think so.)
Big Picture: A Deep State of judges, regulators, politicians and corporations have secretly signed on to "
A New World Order" where government is "disaggregated"

Anne-Marie Slaughter
into self-defined networks. From that point on, their pledges of loyalty to the U.S. Constitution became optional.
In the dramatic up tick in White House polemics about Islam, it becomes important to note that unlike Christianity and Judaism where lying is a sin, Muslims are permitted to lie to Westerners, Jews and Christians. Qur'an 3:28.
Bookmark: #Fig-9

Fig. 9—A New World Order by Anne-Marie Slaughter. Princeton University Press (2004).
Barack Obama's hollow claims of Christian faith, and his embrace of Islam in the White House, would certainly explain why his administration lies without shame to achieve its Slaughter-esque disaggregation goals.
This disaggregation governance philosophy was introduced by Anne-Marie Slaughter to the U.S. State Department on Apr. 12, 2004. She was then a Princeton international law professor and had just published her book, A New World Order (Princeton University Press 2004). In 2009, she served as a chief political advisor to Secretary of State Hillary Clinton (2009-2013).[276]
In evident excitement about the coming presidency of Barack Obama, Princeton re-published the book (never mind that the 2008 election was still two months away). Slaughter's ideas have provided a suitably academic rationale for the institutionalization of crony capitalism and the establishment of a permanent power class for those deemed worthy of an invitation to the networking party ("The Cartel" or "Deep State").
New world order, or just another justification for corruption and crony capitalism?
"
The state is not disappearing, it's disaggregating, meaning it is simply operating through all its different branches, through regulatory agencies, through judges, through legislators, and they are all networking with one another."
—Anne-Marie Slaughter, U.S. Dept. of State speech introducing "A New World Order" Apr. 12, 2004.
The Deep State needed a global technology platform, so they stole Columbus, Ohio innovator Leader Technologies' invention of social networking. Leader's invention overcame inherent "scalability" problems the Deep State was having with legacy IBM, Microsoft and Xerox client-server platforms.
IBM pumped in a $40 million "donation" to The Eclipse Foundation. Leader's patent attorney, James P. Chandler, III (who was also counsel to IBM), secretly fed Leader's invention to Eclipse. Then a Who's Who of companies like SAP, Borland, Cisco, Intel, Oracle, Wind River, Nokia, HP and Microsoft signed up to get Leader's invention at a breathtaking rate.
Leader's invention enabled Eclipse members to unify their "disaggregation" networking efforts around the planet. In his hubris, Harvard Law professor James P. Chandler described his theft of his client's invention for the Deep State as "in the greater good."
A world of interdependent, self-regulating international networks where the U.S. Constitution is in the way
Tellingly, Slaughter never mentions the U.S. Constitution as a guiding principle in her speech introducing A New World Order to the State Department on Apr. 12, 2004. Neither does she mention Leader Technologies on whom she and her cronies rely to pull off their heist.[285]
* * *
"[C]ourts should not make policy or invent rights not stipulated or implied by statutes or the Constitution's text. But courts have no nobler function than that of actively defending property, contracts and other bulwarks of freedom against depredations by government, including by popularly elected, and popular, officials." —George F. Will[001]
"The banking powers are more despotic than a monarchy, more insolent than autocracy, more selfish than bureaucracy."—Abraham Lincoln (1863)
"Those who would give up essential liberty to purchase a little temporary safety, deserve neither liberty nor safety."—Benjamin Franklin (1789)
- Investigators for Americans for Innovation were invited by the International Consortium of Investigative Journalists ("ICIJ") to provide details about Leader Technologies, Inc.’s ("Leader") patent infringement dispute with Mark Zuckerberg and Facebook, Inc. (collectively "Facebook" and/or "Zuckerberg"). This document was prepared in response.
- Leader is a software development company founded in 1997 by engineer-entrepreneur Michael T. McKibben ("McKibben"). McKibben had previously led the redevelopment of the AT&T Access Plus 3.0’s Microsoft Exchange-compatible Windows email system introduced concurrently with Windows 95 in close collaboration with AT&T Bell Labs.
- From inception in 1997 to the present, Leader has developed computer software that has resulted in multiple patents, including U.S. Pat. No. 7,139,761, Dynamic Association of Electronically Stored Information with Iterative Workflow Changes, Nov. 21, 2006—the "secret sauce" technological innovation that is popularly called "social networking."[002]
McKibben's other patents include U.S. Pat. No. 8,195,714 on Jun. 5, 2012, Context Instantiated Application Protocol (the patent on all mobile and desktop apps), Jun. 05, 2012[283] and U.S. Pat. No. 7,925,246, Radio/Telephony Interoperability System, Apr. 12, 2011.[284]
- Bookmark: #leader-petition-for-writ-of-certiorari-overview
Leader sued Facebook on Nov. 19, 2008 for willful patent infringement, damages and injunction ("Leader v. Facebook"). A jury trial was held from Jul. 19-28, 2010 resulting in a split verdict.[003] Leader proved that Facebook infringes Leader’s patent on 11 of 11 claims and that there was no prior art. Facebook prevailed on an "on-sale bar" claim—a claim not asserted until Jun. 24, 2010, three weeks before trial.[004] Leader appealed the on-sale bar verdict to the U.S. Court of Appeals for the Federal Circuit on May 04, 2011,[005] then, when the appeals court failed to apply its own well-settled Pfaff and Group One legal tests, Leader petitioned the U.S. Supreme Court on Nov. 16, 2012, but was denied a hearing on Jan. 7, 2013.[006]
- Bookmark: #fidelity-contrafund-danoff-facebook
Both the Federal Circuit appeal and the U.S. Supreme Court petition were ruled in Facebook’s favor, despite the courts:
(a) Knowledge of egregious denial of due process to Leader,[007]
(b) Multiple notices of the emergence of 28 previously concealed Zuckerberg computer hard drives and Harvard emails; Facebook’s attorney Gibson Dunn LLP[008] (who concealed them) was representing Facebook in the case;[009]

William Danoff, Fidelity Contrafund (Ticker Symbol: FCNTX)
(d) Substantial relationship conflicts of interest among the judges with Gibson Dunn LLP, various other Facebook attorneys, including Cooley Godward LLP,[015] Facebook investors, Leader potential witnesses, the Patent Office and other U.S. government officials and advisers.[016]
Bookmark: #corruptors
Ninety-seven (97) Harvard, Stanford and Yale "disaggregator" sycophants redefining the U.S. Constitution as A New World Order of crony capitalism that they control in secret.
How many Harvard, Stanford and Yale graduates does it take to corrupt global technology, commerce and government? At least four years of investigations conclude: Sixty-five (65) from Harvard, fifteen (15) from Stanford and seventeen (17) from Yale.
Here is the Gallery in alphabetical order:
Bookmark: #Fig-11
Harvard Corruptors (65)

Blankfein

Albright

Ayer

Balmer

Bharara

Blankfein

Bredar

Breyer

Bush, Jr.

Chandler

Chopra

Chuang

Coleman

Cronin

Danoff

Dimon

Doerr

Dyson

Frank

Garland

Gates

Gergen

Gore

Holder

Hughes

Kim

Kocher

Kramer

Lake

Levine

Li

Louie

Menschel

Menschel

Moskovitz

Mogin

Noonan

Park

Patrick

Patrick

Pompeo

Priestap

Pritzker

Reno

Roberts

Romney

Rosenstein

Sandberg

Saverin

Schiff

Seligman

Shirky

Slaughter

Stern

Steyer

Stephens

Summers

Swartz

Tchen

Obama

Obama

Watson

Wittes

Yoo

Zuckerberg
Fig. 11—Harvard University Corruptors: Madeleine J.K. Albright, Donald B. Ayers, Steven A. Balmer, Preetinder "Preet" Bharara, Lloyd C. Blankfein, James K. Bredar, James W. Breyer, George W. Bush, James P. Chandler, Aneesh Chopra, Theodore D. Chuang, William T. Coleman, Michael F. Cronin, William Danoff, Jamie Dimon, John Doerr, Esther Dyson, Barney Frank, Merrick B. Garland, William H. Gates, David R. Gergen, John Hagel III, Eric H. Holder, Chris Hughes, Thomas J. Kim, Robert Kocher, David J. Kramer, Marne L. Levine (Deutch), Ping Li, Gilman Louie, Richard L. Menschel, Sabina Menschel, Paul Mogin, Dustin Moskovitz, Thomas E. Noonan, Todd Y. Park, Diane B. Patrick, Duval L. Patrick, Michael R. Pompeo, William Edward 'Bill' Priestap, Penny S. Pritzker, Janet W. Reno, John G. Roberts, Jr., Rod J. Rosenstein, Sheryl K. Sandberg, Eduardo Saverin, Adam B. Schiff, Nicole Seligman, Clay Shirky, Ann-Marie Slaughter, Donald K. Stern, Thomas F. Steyer, Jay B. Stephens, Lawrence H. Summers, James Swartz, Christina M. Tchen, Michelle L. R. Obama, Barack H. Obama, Derrick K. Watson, Benjamin Wittes, John C. Yoo, Mark E. Zuckerberg.
Bookmark: #Fig-12
Stanford Corruptors (17)

Boswell

Cohler

Davidson

Friedland

Hastings

Hennessy

Hoffman

Jarrett

Karp

Lamont

Lonsdale

Mills

Reines

Rice

Schiff

Thiel

Westly
Fig. 12—Stanford University Corruptors: Eric J. Boswell, Matthew R. Gordon K. Davidson, Michelle T. Friedland, Wilmont Reed Hastings, Jr., John L. Hennessy, Reid G. Hoffman, Valerie J. B. Jarrett, Alexander C. Karp, Ann Huntress Lamont, Joseph T. Lonsdale, Cheryl D. Mills, Edward R. Reines, Susan E. Rice, Adam B. Schiff, Peter A. Thiel, Steve Westly.
Bookmark: #Fig-13
Yale Corruptors (15)

Axelrod

Biden

Bush, Sr.

Bush, Jr.

Clinton

Clinton

Gergen

Goldstein

Koskinen

Mukasey

Richman

Shirky

Sullivan

Woolsey

Yoo
Fig. 13—Yale University Corruptors: Matthew S. Axelrod, R. Hunter Biden, George H. W. Bush, George W. Bush, William J. Clinton, Hillary R. Clinton, David R. Gergen, Andrew D. Goldstein, John A. Koskinen, Michael B. Mukasey, Daniel C. Richman, Clay Shirky, Jake Sullivan, R. James Woolsey Jr, John C. Yoo.
Bookmark: #cia-formed
Bookmark: #1947
1947
-
On Sep. 18, 1947, under the provisions of the National Security Act of 1947 (61 Stat. 495), approved July 26, 1947, effective on September 18, 1947, the National Security Council (NSC) and the Central Intelligence Agency (CIA) were created. The 1947 Act charged the CIA with coordinating the nation's intelligence activities and correlating, evaluating, and disseminating intelligence which affected national security. In addition, the Agency was to perform other duties and functions related to intelligence as the NSC might direct. The Act defined the Director of Central Intelligence's (DCI) authority as head of the Intelligence Community, head of the CIA, and principal intelligence adviser to the President, and made him responsible for protecting intelligence sources and methods. The act also prohibited the CIA from engaging in law enforcement activity and restricted its internal security functions. The CIA carried out its responsibilities subject to various directives and controls by the President and the NSC.[829]
Bookmark: #nsa-formed
Bookmark: #1952
1952
-
On Oct. 24, 1947, President Harry S. Truman issued a memorandum on communications intelligence (COMINT) that authorized the creation of the National Security Agency (NSA). The memorandum instructeds the Special Committee to issue a directive to the Secretary of Defense which defines the COMINT mission of NSA as being to "provide an effective, unified organization and control of the communications intelligence activities of the United States conducted against foreign governments" (and not against American citizens).[830]
Bookmark: #atlantic-council-formed
Bookmark: #1961
1961
- Bookmark: #atlantic-council
In 1961, the Atlantic Council was formed as a think tank for globalist priorities. George Soros heavily subsidizes the activities of this so-called think tank.
Hillary Clinton and the head of CrowdStrike, Dimitri Alperovitch, were both ranking members of the Atlantic Council. Alperovitch is Co-Founder and CTO of CrowdStrike, the computer security company implicated in the deceptions surrounding the alleged hack of DNC servers accused on Russians, but appears to have been a CrowdStrike inside job and false flag designed to frame Donald Trump for alleged Russian interference in the 2016 election. Hillary was awarded the Atlantic Council's Distinguished International Leadership Award in 2013. Bill Clinton received the award in 2010. In 2009, George Bush received the award. Also in 2009, IBM CEO Samuel J. Palmisano received the Award. Palmisano led Barack Obama's Internet of Things fascist public-private conspiracy pursuant to Executive Order 13718 in 2016.

R. James Woolsey Jr.

Samuel J. Palmisano

Dmitri Alperovitch

Hillary Clinton

Evelyn N. Farkas

George Soros
| Atlantic Council Directors (2014) include:[1036] |
| Lastname |
Firstname |
SES Member* |
| Acheson |
David C. |
Yes |
| Albright |
Madeleine J.K. |
Yes |
| Bagley |
Elizabeth F. |
Yes |
| Baker, III |
James A. |
Yes |
| Brown |
Harold |
Yes |
| Carlucci, III |
Frank C. |
Yes |
| Clark |
Wesley K. |
Yes |
| Dodd |
Christopher J. |
|
| Egan, Jr |
Thomas J. |
|
| Gates |
Robert M. |
Yes |
| Hayden |
Michael V. |
Yes |
| Kissinger |
Henry A. |
|
| Mullen |
Michael G. |
|
| Perry |
William J. |
Yes |
| Pickering |
Thomas R. |
Yes |
| Powell |
Colin L. |
Yes |
| Rice |
Condoleezza |
Yes |
| Rowny |
Edward L. |
Yes |
| Shultz |
George P. |
Yes |
| Slaughter |
Anne-Marie |
|
| Taft, IV |
William H. |
|
| Verveer |
Melanne |
Yes |
| Warner |
John W. |
|
| Webster |
William H. |
Yes |
| Woolsey Jr. |
R. James |
|
* If blank, the person may be an SES member, but no corroborating evidence available.
Bookmark: #kennedy-assassinated
Bookmark: #1963
1963
- On Nov. 22, 1963, President John F. Kennedy was assassinated in Dallas, Texas. The Oct. 2017 release of JFK files by President Donald J. Trump revealed that the C.I.A. was involved.
Earlier, sometime after ca. Oct. 28, 1962, President John F. Kennedy said to friends about the CIA Pay of Pigs Cuba debacle, and resulting Cuban Missile Crisis, that he wanted: JFK: “. . . to splinter the C.I.A. in thousand pieces and scatter it to the winds.” New York Times[833]
Bookmark: #church-committee-hearings
Bookmark: #1976
1976
- On Apr. 26, 1976, Sen. Frank Church. Senate Select Committee (The Church Committee) to Study Governmental Operations with Respect to Intelligence Activities. In this hearing, Senator Church exposed the massive and secret C.I.A. MKUltra mind control program. While the Senate ordered the programs to stop, they did not.[1016]
Bookmark: #1978 #ses-created
1978
- On Oct. 13, 1978, The Senior Executive Service (SES) was created as Title IV in the Civil Rights Reform Act of 1978 under President Jimmy Carter.
The Act reformed the civil service of the federal government, partly in response to the Watergate scandal. It abolished the U.S. Civil Service Commission and distributed its functions primarily among four new agencies: the Office of Personnel Management (OPM), the Merit Systems Protection Board (MSPB), the Federal Labor Relations Authority (FLRA) and the Senior Executive Service (SES).

Hillary Clinton

Kristine Marcy
President Carter assigned Kristine Marcy (nee McConnell) to organize the SES. Marcy was and is a notorious lesbian activist close to Hillary Clinton and Janet Reno, among others.[1013] [1014] [1018] [1019]
[1020] [1029]
Bookmark: #1979
1979
SES federal takeover of San Francisco (Silicon Valley). Why? To make the area rogue C.I.A.-friendly
-
On Nov. 07, 1979, then San Francisco Mayor Dianne G.B. Feinstein attempted to start a Senior Executive Service (SES) within the City of San Francisco. Touch & Ross LLP (now Delloitte & Touche) was hired to prepare the selling job for the implementation of SES. Touche & Ross LLP were paid by the federal Office of Personnel Management (OPM) formed just months earlier by the Civil Rights Reform Act of 1978. This effort was clearly one of the first attempts by Kristin Marcy, the newly-appointed director of the SES in Washington D.C. to push this federal program down to not only the state level, but also in major cities—in complete violation of the Hatch Act.

Kristine Marcy

Dianne G.B. Feinstein
Bookmark: #ses-1980-plum-book
1980
-
On Nov. 18, 1980, the House of Representatives published its first "Plum Book" describing the first list of over 8,600 Senior Executive Services (SES) employees titled Policy and Supporting Positions. Committee on Post Office and Civil Service House of Representatives, 96th Congress, 2d Session. Y 4.G 74/7 :P 75/6/980. GPO.[1039]
On Oct. 13, 1978, The Senior Executive Service (SES) was created as Title IV in the Civil Rights Reform Act of 1978 under President Jimmy Carter.
| 1980 Plum Book includes:[1036] |
| No. |
Lastname |
Firstname |
| 1 |
Babbitt |
Bruce |
| 2 |
Bradley |
Thomas |
| 3 |
Bremer |
L. Paul |
| 4 |
Brzezinski |
Zbigniew K. |
| 5 |
Bundy |
McGeorge |
| 6 |
Carlucci |
Frank C. |
| 7 |
Holbrooke |
Richard |
| 8 |
Kennedy |
Patrick F. |
| 9 |
Lake |
William T. |
| 10 |
Marshall |
Andrew W. |
| 11 |
Muskie |
Edmund S. |
| 12 |
Pickering |
Thomas R. |
| 13 |
Rockefeller |
Sharon P. |
| 14 |
Scowcroft |
Brent |
| 15 |
Volcker |
Paul A. |
| 16 |
Warren |
Christopher |
| 17 |
Watson, Jr. |
Thomas J. (IBM - Moscow) |
Bookmark: #ses-1984-plum-book
1984
-
On Nov. 22, 1984, the House of Representatives published its first "Plum Book" describing the first list of over 8,000 Senior Executive Services (SES) employees titled Policy and Supporting Positions. Committee on Post Office and Civil Service House of Representatives, 96th Congress, 2d Session. Y 4.G 74/7 :P 75/6/980. GPO.[1035]
On Oct. 13, 1978, The Senior Executive Service (SES) was created as Title IV in the Civil Rights Reform Act of 1978 under President Jimmy Carter.
| 1984 Plum Book includes:[1035] |
| No. |
Lastname |
Firstname |
| 1 |
Armitage |
Richard K. |
| 2 |
Ayer |
Donald B. |
| 3 |
Baker III |
James A. |
| 4 |
Balridge |
Malcolm |
| 5 |
Bork |
Robert H. |
| 6 |
Breyer |
Stephen G. |
| 7 |
DiGenova |
Joseph E. |
| 8 |
Farnan, Jr. |
Joseph J. |
| 9 |
Ginsburg |
Ruth Bader |
| 10 |
Jackson |
Thomas Penfield |
| 11 |
Marshall |
Andrew W. |
| 12 |
Meese III |
Edwin |
| 13 |
Olson |
Theodore B. |
| 14 |
Orrick Jr. |
William H. |
| 15 |
Scalia |
Antonin |
| 16 |
Sessions III |
Jefferson B. |
| 17 |
Starr |
Kenneth W. |
| 18 |
Taft IV |
William H. |
| 19 |
Webb |
Dan K. |
| 20 |
Weinberger |
Casper W. |
Bookmark: #shadowy-government
Bookmark: #1987
1987
- On Aug. 03, 1987, Senator Daniel K. Inouye (HI) chaired the Senate Select Committee on Secret Military Assistance to Iran and the Nicaraguan Opposition, which held public hearings on the Iran-Contra affair. Senator Inouye, summarizes here the coverup of the US Shadowy Government involvement; by saying:[798]
"There exists a shadowy Government with its own Air Force, its own Navy, its own fundraising mechanism, and the ability to pursue its own ideas of the national interest, free from all checks and balances, and free from the law itself."
Bookmark: #ses-1988-plum-book
1988
-
On Nov. 22, 1984, the House of Representatives published its first "Plum Book" describing the first list of over 8,000 Senior Executive Services (SES) employees titled Policy and Supporting Positions. Committee on Post Office and Civil Service House of Representatives, 96th Congress, 2d Session. Y 4.G 74/7 :P 75/6/980. GPO.[1035]
On Oct. 13, 1978, The Senior Executive Service (SES) was created as Title IV in the Civil Rights Reform Act of 1978 under President Jimmy Carter.
| 1988 Plum Book includes:[1035] |
| No. |
Lastname |
Firstname |
| 1 |
Armitage |
Richard K. |
| 2 |
Ayer |
Donald B. |
| 3 |
Baker III |
James A. |
| 4 |
Balridge |
Malcolm |
| 5 |
Bork |
Robert H. |
| 6 |
Breyer |
Stephen G. |
| 7 |
DiGenova |
Joseph E. |
| 8 |
Farnan, Jr.* |
Joseph J. |
| 9 |
Ginsburg |
Ruth Bader |
| 10 |
Jackson |
Thomas Penfield |
| 11 |
Marshall |
Andrew W. |
| 12 |
Meese III |
Edwin |
| 13 |
Olson |
Theodore B. |
| 14 |
Orrick Jr. |
William H. |
| 15 |
Scalia |
Antonin |
| 16 |
Sessions III |
Jefferson B. |
| 17 |
Starr |
Kenneth W. |
| 18 |
Taft IV |
William H. |
| 19 |
Webb |
Dan K. |
| 20 |
Weinberger |
Casper W. |
| * Judge Joseph J. Farnan was the first trial lawyer who devastated Facebook at the Markman Hearing of Leader v. Faebook. He was replaced just one month before trial by Obama nominee Leonard P. Stark just one month before trial, after which Stark allowed Facebook to completely change its claims and barred Leader from additional discovery in an evident abuse of due process. |
Bookmark: #rise-of-spy-state-oligarchy
Bookmark: #1990
1990-1999
- In 1990, Lawrence "Larry" Summers, a professor of economics at Harvard, tutored a favorite student, Sheryl K. Sandberg, while fellow professor of law, James P. Chandler, III, looked on. In their hubris, they have used their inside knowledge of America's legal and economic weaknesses to try and create a permanent ruling class among their cronies.

Larry H. Summers

Sheryl K. Sandberg

Yuri Milner

James P. Chandler
Yellow symbol is metaphorical irony likening lawyers to hazardous substances. Photos L/R/T/D: Life, ABC News, Fortune, NIPLI, Freeze Corp, Politico, Daily Caller, Sanpedronewspilot.

James E. Freeze
Overview
A "public-private" plan to privatize the management of American security and intelligence appears to have hatched from this Chandler-Freeze association in the early 1990's.
On Jun. 07, 1993—five months into Bill Clinton's first term as President in 1993—Clinton advisors James P. Chandler and John D. Podesta hosted an encryption conference in Washington, D.C.
The clear objective of that conference was to create a rationale to give Clinton's Deep State intelligence people a universal backdoor key to all digital communications.
During 1993-1994, Bill & Hillary Clinton's political enemies were being killed of like flies, as revealed by their long term Arkansas political "fixer," Larry Nichols, producer of The Clinton Chronicles (1994).
Tellingly, on Apr.
17, 1995, Bill Clinton signed Executive Order No. 12958[271] Classified National Security (first published on Jan. 01, 1995). This order appears to be the legal genesis for an illegal Deep C.I.A. Spy State run out of the White House used to gather dirt on individuals across the planet. Chandler very evidently wrote this executive order and provided the continuity for this illegal agency through the Clinton, Bush and Obama presidencies.
During this time, Chandler and Freeze privately formed and repeatedly flipped a company named Eurotech, Ltd. that supplies software and hardware to the spy state. A decade later, they both served as directors for Columbus innovator, Leader Technologies, until that is, Chandler took custody of a copy of Leader's source code on June 05, 2002 and that code then magically appeared in the "open source" programming code of the IBM Eclipse Foundation just 11 weeks later.
Leader Technologies invention was social networking (which these spy state aficionados clearly wanted for their schemes). It solved a "scalability" problem that Microsoft's, IBM's and Xerox's older client-server architectures were choking on.

David J. Kappos
Leader's innovations were sent immediately to Chandler's long-time crony client and technology supplier to the secret Deep State—IBM, where the future Patent Office director David J. Kappos was waiting for it. As just stated, eleven weeks later, Leader's innovations first appeared in IBM's Eclipse Foundation release 2.0.1 with illegal IBM copyright claims. Eighteen months later, with Larry Summers now its president, Facebook emerged at Harvard. Facebook was just the first of numerous NSA data gathering fronts to emerge from IBM Eclipse, a ring leader in this scheme.
It would be macabre if their choice of "The Eclipse Foundation" name alluded to the damage done by their in-your-face eclipse of the U.S. Constitution.
Behind this national security smokescreen (it's for the greater good), these men concocted a legal sophistry that lured American citizens into agreeing to give away their sacred Constitutional rights to privacy in exchange for "free" online services.
With these "end user license agreements" in hand, the NSA was given the legal clearance to spy on Americans. Much, if not most, of this legal vision is the brainchild of James P. Chandler, who now operates a fifth column within the Obama Administration, probably even vetting all FOIA requests for the White House.

Bill J. Clinton
Chandler is the author of the Economic Espionage Act of 1996 under Bill Clinton. One of Bill Clinton's last acts as president was to appoint Chandler to the National Infrastructure Assurance Council ("NIAC") just two days before he left office on Jan. 20, 2001.[024] Chandler directed ongoing traffic for this spy state agenda, starting under Clinton, through Bush, and now under Obama.
To facilitate the "Big Data" collection, these three presidential administrations cleared the regulatory path ways for Wall Street and Silicon Valley to form companies to give the illusion of choice—but don't be fooled, they are all NSA "old boy" creations.

James P. Chandler, III
Indeed, Washington, D.C. insiders report that a central actor in this corruption, Clinton security adviser James P. Chandler, has famously declared that the "prime" defense contractors (Boeing, Lockheed, Northrop Grumman, General Dynamics and Raytheon) are merely revolving door agencies of the federal government. Chandler has merely extended his philosophy of an insider's game to the control of the Internet, exhibited by the NSA's abuse of privacy.
The legislative, executive, judicial and Free Press institutions of our Republic stopped working as designed
The quid pro quo for American intelligence under the Executive branch was that these private companies would feed funds and data to the NSA and government insiders without Congressional approval (the Legislative branch). Blackmail, extortion, intimidation and coercion by insiders is inescapable. It is just what bad people do.
The quid pro quo for the cooperation of the Judicial branch was new wealth from specially organized Wall Street mutual funds and waiver of judicial ethics rules that would look the other way when these mutual funds were disclosed. What judge or judicial employee will resist the tipsters subsequently?

Hillary R. Clinton
The quid pro quo for the Free Press was income from advertising and voter manipulation. In exchange, the "lame stream media" stopped holding the powerful accountable because the Silicon Valley purveyors of "Big Data" and their bankers fed them advertising. They have become data junkies. Sadly, the press began using the unverified "narratives" of the spy state conspirators as their primary sources, thus reinforcing the lies. The Social Network is a perfect example of a lying "narrative" about Mark Zuckerberg and Facebook that the public believed because the mainstream media never questioned its veracity.

Anne-Marie Slaughter
Constitutional checks and balances have degenerated into competing oligarchies and secret alliances
In short, this "public-private partnership" scheme pressed by Hillary Clinton adviser, Anne-Marie Slaughter ("A New World Order"), has destroyed Constitutional checks and balances. In its place are unaccountable spy state oligarchies based on ill-conceived and self-serving "international networks."
Bookmark: #Fig-15

Fig. 15—Public-Private Partnership to Destroy Liberty & Privacy. L/R: Blog, Tumblr (Yahoo), Twitter, Flickr (Yahoo), Instagram (Facebook), Facebook, Google+, YouTube (Google). All members of IBM's Eclipse Foundation and, according to NSA documents leaked by patriot whistle blower, Edward Snowden,
[187] all members of the NSA Deep Spy State cartel and IBM's Eclipse Foundation.. Bottom line Twitter, Yahoo, Facebook and Google run the spy state apparatus for the NSA, along with AT&T, Verizon and Microsoft (Skype).
The State Department's website is a good example of the ubiquity of the NSA spy state user data gathering juggernaut:
- Between 1990-1992, Russian Yuri Milner obtained an MBA from the Wharton School of Business.
- Bookmark: #paul-kagame-cia-trained
Rogue C.I.A. shadow government planned to secure diamonds and rare earth minerals needed for manufacturing in computers, TVs, mobile phones, space and defense in Central Africa by installing Paul Kagame as a strongman, no matter the human cost

Paul Kagame, C.I.A. Agent

Fig. 3—
Rwandan Paul Kagame (right). At the time of the October 1990 invasion of Rwanda, Paul Kagame was being trained by the globalist rogue C.I.A. at the Pentagon's General Staff and Command College at Fort Leavenworth, in Kansas (USA). Kagame returned and led the four year war that resulted in the deaths of perhaps several hundred thousand Hutu people between October 1990 and April 1994 alone. From
Keith Harmon Snow. (Apr. 05, 2012). Pentagon Produces Satellite Photos Of 1994 Rwanda Genocide, p. 4.
Conscious Being Alliance.
Bookmark: #1991
1991
- Bookmark: #bush-new-world-order-1991

George H.W. Bush
George H.W. Bush, C.I.A. Director (1976-77) announced "A New World Order"
On Jan. 16, 1991, in his Oval Office address to the nation announcing the first Persian Gulf War, President George H.W. Bush telegraphed the Deep State shadow government agenda to use a destabilized Middle East to usher in a globalist "New World Order" that would be run by un-elected bureaucrats, bankers and multi-national corporations. This agenda has emerged out of such globalist organizations as the Trilateral Commission, Bilderberg Group, Bohemian Grove, European Union, rouge C.I.A., rogue NSA, Yale Skull & Bones, Council on Foreign Relations (CFR) and the World Economic Forum (Davos). In short, the self-anointed "elites" want to destroy the Grand American Experiment in a Republic where all power emerges from the People, the Governed, and not from oligarchs, monarchs, bureaucrats, lawyers and dictators.[616]
''This is an historic moment. We have in this past year made great progress in ending the long era of conflict and cold war. We have before us the opportunity to forge for ourselves and for future generations a new world order — a world where the rule of law, not the law of the jungle, governs the conduct of nations. When we are successful — and we will be — we have a real chance at this new world order, an order in which a credible United Nations can use its peacekeeping role to fulfill the promise and vision of the U.N.'s founders."
- Bookmark: #globalbaloney

Sheryl K. Sandberg

Lawrence "Larry" H. Summers
-
In 1991, Sheryl K. Sandberg became a research assistant to Lawrence "Larry" Summers at the World Bank
after Summers had been her senior thesis advisor.[401]
Bookmark: #Fig-16
Larry Summers' reckless "Big Bangery" and "Globaloney" Harvard economic theories laid the foundation for this New World Order corruption, which is age-old fraud and greed dressed up in the latest elitist hubris.
- Between 1991-1993, "wunderkind professors of economics" including Larry Summers were unleashed as "ersatz policy
'experts'" by the World Bank to implement their "flawed" plan for privatization of banking in the Soviet Union ("Big Bangery" and "globaloney" to justify the monopolistic world-wide role of the World Bank."). This reckless voucher system resulted in the emergence of the current system of corrupt Russian oligarchies controlled by the Kremlin; oligarchies that Summers, Sandberg and Milner now exploit.[268]

Yuri Milner

Alisher Usmanov

Lloyd Blankfein
Bookmark: #dan-casolaro
Hillary R. Clinton

William J. Clinton
,
Dan Casolaro, a journalist investigating Bill and Hillary Clinton's involvement in ADFA (Arkansas Development Finance Authority) and their Mena, Arkansas $100 million drug smuggling and money laundering operation, allegedly committed suicide.
[528]
- Bookmark: #sandberg-anti-patriarchy

Sheryl K. Sandberg

Lawrence "Larry" H. Summers
Bookmark: #1992
1992
Bookmark: #victor-raiser
Hillary R. Clinton

William J. Clinton
,
Victor Raiser & son, chair of the Clinton Presidential Finance Committee, died in a plane crash.
[528]
- Bookmark: #ruby-ridge
From Aug. 21 - 31, 1992, Ruby Ridge was the site of a deadly confrontation and an eleven-day siege near Naples, Idaho, beginning on August 21, 1992, between Randy Weaver, members of his immediate family and a family friend Kevin Harris, and agents of the United States Marshals Service (USMS) and the Hostage Rescue Team of the Federal Bureau of Investigation (FBI HRT).
According to Ted L. Gunderson, FBI Special Agent In Charge (ret.), this event was staged by the government and was a wholly unwarranted response to a loyal American, Randy Weaver, who lived remotely with his wife, Vicki, and daughter, simply refusing to appear for a court hearing after a summons had been issued.
[639] See Ted L. Gunderson's timeline entry for
May 12, 2005.
- Bookmark: #george-soros-crashed-uk-pound

George Soros
, hedge fund manager George Soros famously bet against the UK pound. Hedge funds were not yet well known.
In a nutshell, Soros believed that the British Pound was overvalued and was headed for a devaluation. So, he borrowed over ten billion Pounds in a 'Go for the jugular' move. He then immediately converted the Pounds into German Marks. When the markets learned about Soros’ actions, other traders followed suit. This run o the Pound triggered a devaluation. Soros then used his Marks to buy back the now devalued Pounds and
pocketed $1.4 billion profit. All in one day.
Soros fleeced $1.4 billion from the British taxpayer in 1993

Fig.–George Soros went "for the jugular" and almost destroyed the British economy in 1992.
Source: INBU 4200 Int’l Financial Management.
Soros would go on to repeat this money market manipulation across the world for decades. These funds were used to finance Bill & Hillary Clinton, The Clinton Foundation, The Clinton Global Initiative, Barack Obama, his takeover of the U.S. Democratic Party and his Open Society Foundations globalist "new world order" political agenda.
[437]
See also December 20, 1998 (below)
George Soros being interviewed by Steve Kroft of CBS 60 Minutes about this UK pound and other admitted market corruption.

William J. Clinton
, William ("Bill") J. Clinton elected 42nd U.S. President.
- Bookmark: #ses-1992-plum-book
On Nov. 10, 1992, the Senate published the fourth "Plum Book" describing over 8,600 Senior Executive Services (SES) employees titled Policy and Supporting Positions. Committee on Governmental Affairs, 102d Congress, 2d Session. Y 4.G 74/9: S. Prt. 102-509. ISBN 0-16-039526-7. GPO.[1041]
On Oct. 13, 1978, The Senior Executive Service (SES) was created as Title IV in the Civil Rights Reform Act of 1978 under President Jimmy Carter.
| 1992 Plum Book includes:[1041] |
| No. |
Lastname |
Firstname |
| 1 |
Addington |
David S. |
| 2 |
Alexander Jr. |
Andrew Lamar |
| 3 |
Baker III |
James A. |
| 4 |
Bork, Jr. |
Robert H. |
| 5 |
Chao |
Elaine |
| 6 |
Cheney |
Richard B. |
| 7 |
Cheney |
Lynne V. |
| 8 |
Keating II |
Francis A. |
| 9 |
Libby |
I.L. "Scooter" |
| 10 |
Mueller III |
Robert S. |
| 11 |
Roberts, Jr. |
John G. |
| 12 |
Rockefeller |
John D. |
| 13 |
Rockefeller, Jr. |
Nelson A. |
| 14 |
Schall |
Alvin A. |
| 15 |
Schapiro |
Mary L. |
| 16 |
Sessions |
William S. |
| 17 |
Terwilliger III |
George J. |
| 18 |
Watkins |
James D. |
Bookmark: #1993
1993

William J. Clinton

William J. Clinton

Hillary R. Clinton

Marne L. Levine (later Deutch)

Lawrence "Larry" H. Summers

Hillary R. Clinton
- Bookmark: #world-trade-center-bombing
 On Feb. 26, 1993
On Feb. 26, 1993, The 1993 World Trade Center bombing was alleged to be a terrorist attack on the World Trade Center. A truck bomb detonated below the North Tower of the World Trade Center in New York City. The 1,336 pounds (606 kg) urea nitrate–hydrogen gas enhanced device
(supplied by an FBI Informant, see below) was intended, according to the official propaganda narrative, to send the North Tower (Tower 1) crashing into the South Tower (Tower 2), bringing both towers down and killing tens of thousands of people. It failed to do so, but killed six people and injured over a thousand.
According to Ted L. Gunderson, FBI Special Agent In Charge (ret.), the FBI had infiltrated the terrorist cell through FBI Informant Emad Salem. Salem was tasked with building the bomb. Salem recorded the meetings with his FBI handlers who supplied the bomb, much to his surprise. In other words, this bombing was planned and carried out by the FBI who allowed the terrorists to proceed. Gunderson believes the microphone recording is the only defense that Salem had against being framed and sent to prison.
[639] See Ted L. Gunderson's timeline entry for
May 12, 2005.
- Bookmark: #lebleu-mckeaham-williams-willis

Janet W. Reno

Hillary R. Clinton

William J. Clinton
,
C. LeBleu, T. McKeaham, R. Williams, S. Willis, bodyguards for Bill and Hillary Clinton, were all killed by gunfire in the illegal Waco, Texas raid on the David Koresh Branch Davidian compound. Attorney General Jaent Reno ordered the evidently illegal attack
[528]
According to Ted L. Gunderson, FBI Special Agent In Charge (ret.), these men were all shot in the head in evident assassinations, not at the hands of the Branch Davidians, who took the wrap and some are serving life prison sentences after being framed.
[639]
See Ted L. Gunderson's timeline entry for
May 12, 2005.
- Bookmark: #barkley-hassey-reynolds-sabel

Hillary R. Clinton

William J. Clinton
,
W. Barkley, B. Hassey, S. Reynolds, T. Sabel, bodyguards for Bill and Hillary Clinton, were killed in a helicopter crash.
[528]
- Bookmark: #john-wilson

Hillary R. Clinton

William J. Clinton
,
John A. Wilson, Washington, D.C. councilman died mysteriously as he was preparing to expose the Clintons.
[528]
- Bookmarks: #jun-07-1993-fbi-podesta-chandler-cisco-nsa-cia-backdoor-key-attempted
#crypto-treason
Ground Zero of Obama's ICANN give away TREASON (Oct. 01, 2016) & NSA warrantless surveillance
NSA is "Wrongdoing Masquerading as Patriotism."
—
James Bamford, NSA whistleblower, attendee[519], Clinton, Bush, Obama consiglieri
James P. Chandler III and Chief of Staff
John D. Podesta, via the
Carnegie Endowment for International Peace, sponsored the "Third CPSR Cryptography and Privacy Conference" to gather intelligence with the objective:
"to require that telecommunications manufacturers and service providers redesign their systems to facilitate wiretapping."[519]

James Bidzos, RSA, Verisign (Clinton, Bush, Obama), NSA

Sol Glasner, Mitre (Clinton, Bush, Obama), NSA, The JASON Group

Addison M. Fischer, Verisign (Bush, Obama), NSA

Steven B. Lipner, Mitre, The JASON Group, Microsoft (1999-2015), Bush, Obama), NSA

Stuart Kern (Larry Summers, Clinton, Obama), Treasury Dept.

David R. Johnson, Wilmer Hale (Clinton, Obama) lawyer

Lee Tien, Electronic Frontier Foundation (EFF), likely agent (Clinton, Bush, Obama)

Allan E. Suchinsky, State Dept. (Obama) Export Licensing

John D. Sonderman, State Dept. (Obama) Export Control

Kenneth A. Mendelson, Stroz Friedberg (Obama) U.S. Att. Preet Bharara

Martina L. Bradford, Harry Reid (Obama) AT&T

Stephen Wolff, Cisco, Internet2 (Obama CEO Council)

Catherine M. Russell, US Ambassador for Women (Obama)

Juan P. Osuna, US DOJ, Director, Immigration Review (Obama)

Phil Karn, Qualcomm (Obama CEO Council)

John T. Brennan, Tom Guidoboni, NSA Cyber (2008-2009) (Obama)

Ann M. Harkins, Podesta Assoc, (Obama) Chief of Staff for Att. Gen. Janet Reno (1999-2001)

Stephen D. Crocker, ICANN Chair (current) (Obama); McAfee Internet Security; Highlands

James P. Chandler, III (Clinton, Bush, Obama)

John D. Podesta (Obama)

William J. Clinton

Hillary R. Clinton
Names highlighted below are some of the attendees who enjoy present day Obama Administration relationships that were required to have been disclosed
before any decisions related to ICANN were made on Oct. 01, 2016 where attended Stephen D. Crocker is the chairman.
Summary: These attendees fanned out in all directions. They have massively enriched themselves and their military-industrial co-conspirators. The
quid pro quo for their enrichment was to give a
universal backdoor key to the NSA. Bill & Hillary Clinton, George Bush and Barack Obama each facilitated this organized crime.
| Last_Name |
First_Name |
Organization |
| Adams |
Charlotte |
FCW (Federal Technology) |
| Adams |
John |
IEEE Spectrum |
| Autrey |
Michael |
Privacy Times |
| Baker |
Brian |
CUA Law School (Catholic University of America) |
| Baker |
Stewart |
NSA (National Security Agency) |
| Bamford |
James |
NSA, ABC World News Tonight |
| Banisar |
David |
CPSR (Computer Professionals for Social Responsibility) |
| Barry |
Mikki |
Intercon Systems |
| Berman |
Jerry |
Electronic Frontier Foundation (EFF) |
| Bidzos |
Jim |
RSA, Verisign |
| Bieber |
Denis |
SecurTech |
| Bortnick |
Jane |
Congressional Research Service |
| Bradford |
Martina |
AT&T |
| Brennan |
John T. |
NSA Cyber (Obama) |
| Brooks |
Clint |
NSA |
| Brown |
Reese |
Journal of Intelligence and Counter-Intelligence |
| Bryen |
Steven |
SecurTech |
| Burnham |
David |
TRAC |
| Camp |
Jean |
IEEE |
| Casser |
Karen |
REDACTED |
| Chandler |
James |
George Washington University, Counsel to IBM, NSA, Leader Technologies |
| Charles |
Dan |
NPR |
| Chaum |
David |
DigiCash |
| Cohen |
John |
House Judiciary Committee |
| Cook |
Dan |
Department of State |
| Cornley |
Sarah |
REDACTED |
| Crocker |
Steven |
TIS (Trusted Information Systems now McAfee); ICANN Chairman; Highlands Group/Forum |
| Crowe |
Colin |
House Telecomm |
| Dempsey |
Jim |
House Judiciary Committee |
| Denning |
Dorothy |
Georgetown University |
| Diffie |
Whitfield |
Sun Microsystems |
| Einaudi |
Mario |
CPSR |
| Evans |
Woody |
US West |
| Farber |
David |
Upenn |
| Fischer |
Addison |
Fischer International; Verisign |
| Flaherty |
David |
Wilson Center |
| Frazier |
Greg |
House Committee on Intelligence |
| Gellman |
Bob |
House Government Operations Committee |
| Gilbert |
Frank |
REDACTED |
| Gilmore |
John |
Cygnus Support |
| Glasner |
Sol |
Mitre, The Jason Group |
| Goldman |
Janlori |
ACLU |
| Goodman |
Harry |
NPR |
| Guidoboni |
Tom |
John T. Brennan NSA Cyber |
| Harkins |
Ann |
Senate Judiciary Committee, Podesta Associates |
| Hendricks |
Evan |
US Privacy Council |
| Herman |
Ezra |
BNA |
| Hoffman |
Lance |
George Washington University |
| Hyland |
Paul |
CPSR |
| Johnson |
David |
Wilmer, Cutler & Pickering, now Wilmer Hale |
| Kahn |
David |
Newsday |
| Kallstrom |
James K. |
FBI |
| Kammer |
Ray |
NIST |
| Karn |
Phil |
Qualcomm |
| Kern |
Stuart |
Department of Treasury, Larry Summers |
| King |
Jack |
BNA Legal Report |
| Kurz |
Rob |
House Government Operations Committee |
| Levy |
Steven |
MacWorld |
| Lin |
Herb |
National Academy of Sciences |
| Lipner |
Steve |
Mitre, The JASON Group, Microsoft |
| Madsen |
Wayne |
Computer Sciences Corp |
| Mailman |
Fred |
HP |
| Markoff |
John |
New York Times |
| Martin |
Kate |
CNSS/ACLU |
| McDonald |
Alan |
FBI |
| McGee |
Kate |
Oracle |
| McMullen |
John |
Newsbytes |
| McNulty |
Lynn |
NIST |
| Meeks |
Brock |
Communications Daily |
| Mendelson |
Ken |
House Judiciary Committee; Stroz Friedberg (SDNY) |
| Messmer |
Ellen |
Network World |
| Mintz |
John |
Washington Post |
| Murray |
William |
Deloitte & Touche |
| Nelson |
Mike |
OSTP (White House Office of Science and Technology Policy) |
| Osuna |
Juan |
CRA, DOJ Immigration Oversight |
| Pauli |
Bill |
Apple Computer |
| Peterson |
Beverly |
GAO |
| Peyton |
David Y. |
ITAA |
| Podell |
Harold |
GAO/OSI |
| Podesta |
John |
White House |
| Poulis |
Bill |
Apple Computer |
| Rarog |
Bob |
Digital Equipment Corp. |
| Ratcliffe |
Mitch |
MacWeek |
| Relyea |
Harold |
Congressional Research Service |
| Richelson |
Jeff |
National Security Archive |
| Rosenthal |
Ilene |
Software Publishers Association |
| Rotenberg |
Marc |
CPSR |
| Rudolph |
Debbie |
IEEE |
| Russell |
Cathy |
Senate Judiciary Committee, US Ambassador for Women |
| Schiller |
Jeff |
MIT |
| Schwartau |
Wynn |
Inter*Pak |
| Schwartz |
John |
Washington Post |
| Smith |
Bob |
Privacy Journal |
| Smoot |
Olly |
CBEMA |
| Sobel |
David |
CPSR |
| Sonderman |
John |
Department of State, export control |
| Stapleton |
Ross |
CIA |
| Stern |
Gary |
ACLU |
| Suchinsky |
Allan |
Department of State, export licensing |
| Thomsen |
Roszel |
McKenney, Thomsen & Burke |
| Tien |
Lee |
REDACTED, EFF |
| Wayner |
Peter |
Georgetown University |
| Weingarten |
Rick |
Computer Research Association |
| Whitehurst |
William |
IBM |
| Wolff |
Steven |
NSF, Cisco, Internet2 |
| Zimmermann |
Phil |
Boulder Software Engineering |
- Bookmark: #phil-wilcher

Hillary R. Clinton

William J. Clinton
, Phil Wilcher, Washington, D.C. attorney investigating Bill and Hillary Clinton's drug smuggling and money laundering in Mena, Arkansas, allegedly committed suicide.
[528]
- Bookmark: #vincent-foster

Hillary R. Clinton

William J. Clinton
, Vincent Foster, Jr., Deputy White House counsel and Clinton childhood friend, allegedly committed suicide.
[528]
- Bookmark: #jon-walker

Hillary R. Clinton

William J. Clinton
, Jon Walker, Senior RTC (Resolution Trust Corporation) specialist investigating Whitewater, allegedly committed suicide.
[528]
- Bookmark: #heard-dickson

Hillary R. Clinton

William J. Clinton
, S. Heard, S. Dickson, Clinton's healthcare advisory committee members, died in a plane crash.
[528]
- Bookmark: #luther-parks

Hillary R. Clinton

William J. Clinton
, Luther 'Jerry' Parks, Bill & Hillary Clinton's chief of security at the Clinton campaign headquarters, was murdered.
[528]
- Bookmark: #ed-willey

Hillary R. Clinton

William J. Clinton
, Ed Willey, Bill & Hillary Clinton's manager of the Clinton Presidential campaign finance committee, allegedly committed suicide.
[528]
- Bookmark: #summers-milner-sandberg-1993

Sheryl K. Sandberg

Lawrence "Larry" H. Summers

Yuri Milner
, Larry Summers with Sheryl Sandberg’s assistance engaged then-Wharton MBA student, Russian Yuri Milner, to write the World Bank paper "Voucher Investment Funds" dvocating the Russian voucher system
[128] in their "insane and unnecessary haste."
[267]
Bookmark: #1994
1994

Yuri Milner
- Bookmark: #milner-bank-menatep
In 1994, Yuri Milner met Russian oligarch Mikhail Khodorkovsky. Milner returned to Russia to work with Khodorkovsky at his bank, Bank Menatep, which in 1999 diverted $4.8 billion in IMF funds.[269] This money-laundering of an estimated $10 billion by the Russian mob via Bank Menatep also involved World Bank funds. Tellingly, Yuri Milner does not disclose this association in any of his current biographies. Milner’s activities between 1994 and 2007 are murky.[270]
- Bookmark: #herschel-friday

Hillary R. Clinton

William J. Clinton
, Herschel Friday, a member of Bill & Hillary Clinton's Presidential campaign finance committee, died in a plane crash.
[528]
- Bookmark: #ronald-rogers

Hillary R. Clinton

William J. Clinton
, Ronald Rogers, was killed enroute to an interview for
The Clinton Chronicles.
[528]
- Bookmark: #conspiracy-of-silence
Conspiracy of Silence: Pedophilia blackmail binds the Deep State
shadow government's evil power
On May 03, 1994, TV Guide listed the Yorkshire TV documentary
Conspiracy of Silence was scheduled to air on the Discovery Channel. This documentary exposed a network of religious leaders and Washington politicians who flew children to Washington D.C. for sex orgies. Many children suffered the indignity of wearing nothing but their underwear and a number displayed on a piece of cardboard hanging from their necks when being auctioned off to foreigners in Las Vegas, Nevada and Toronto, Canada
At the last minute before airing, unknown Congressmen threatened the TV Cable industry with restrictive legislation if this documentary was aired. Almost immediately, the rights to the documentary were purchased by unknown persons who had ordered all copies destroyed.
A copy of this videotape was furnished anonymously to former Nebraska state senator and attorney John De Camp who made it available to retired FBI Agent Ted L. Gunderson. While the video quality is not top grade, this tape is a blockbuster in what is revealed by the participants involved.
[642] Click here for Ted Gunderson's Biography PDF.
[644]
- Bookmark: #kathy-ferguson

Hillary R. Clinton

William J. Clinton
,
Kathy Ferguson, former wife of Clinton bodyguard Danny Ferguson, allegedly committed suicide.
[528]
- Bookmark: #bill-shelton

Hillary R. Clinton

William J. Clinton
, Bill Shelton, Arkansas State Police officer, fiance of Kathy Ferguson, former wife of Clinton bodyguard Danny Ferguson, allegedly committed suicide.
[528]
- Bookmark: #clinton-makes-fascism-policy
FASCISM WAS IMPLEMENTED BY THE CLINTON WHITE HOUSE

Bill Clinton made fascist crony capitalism his policy, led by the White House with the C.I.A., NSA, State, Justice and Defense Departments

Hillary R. Clinton

William J. Clinton
, President Bill Clinton wrote “A National Security Strategy of Engagement and Enlargement.” Clinton actually authorized the C.I.A. and NSA to use their super-secret and illegal Echelon Program (started in 1947) to assist American private companies with whom he and Hillary were aligned in pay-to-play schemes.
[951] [952] [953]
Clinton made fascism policy.
He and Hillary set in motion the destruction of the core institutions of the American Republic.

James P. Chandler, III, Harvard/GWU Law, Clintons', Bush's, Obama's intelligence, intellectual property, espionage & national security advisor/rogue C.I.A. consiglieri
PDF p. 12: “Countering terrorism effectively requires close day-to-day coordination among Executive Branch agencies. The Departments of State, Justice and Defense, the FBI and CIA continue to cooperate closely...”
PDF p. 19: “Partnership with Business and Labor: Our economic strategy views the private sector as the engine of economic growth. It sees government’s role as a partner to the private sector – acting as an advocate of U.S. business interests; leveling the playing field . . . ”
Who's "playing field" was being leveled?
The American Republic's & humanity's.
- Bookmark: #clinton-rwanda-pretext
NOTICE: This timeline entry on Rwanda is longer than our normal entries due to an evident and concerted effort by MSM to push a false narrative on the public about who was really behind the merciless slaughter of 1 million innocent civilians. That narrative is evidently a false flag pretext created by a rogue C.I.A. on behalf of its globalist mining and eugenics interests. This entry attempts to straighten a very crooked record that shockingly winds back to Arkansas and the Clintons.
Click to enlarge

John M. Deutch,
C.I.A. Director, pardoned by Clinton for illegal use of computer at home

Paul Kagame
, Paul Kagame took power in Rwanda after an alleged "Rwandan Genocide." This massacre of almost 1 million Rwandans now appears to have been a C.I.A.-fabricated eugenics program that also served as a false flag pretext. This pretext provided the cover to seize control of rare earth minerals in the resource-rich neighboring Congo. Those minerals are critical for the manufacturing of computers, military surveillance devices, aerospace, defense, nuclear, satellites, mobile technology and TVs by the rogue C.I.A. Deep State shadow government "Big Data" spy operation globally.
Kagame had been head of military intelligence in the Ugandan Armed Forces after being
trained by the C.I.A. at the U.S. Army Command and Staff College (CGSC) in Leavenworth, Kansas.
Tellingly, the official "Rwandan genocide" mainstream media and Congressional narrative MAKES NO MENTION of Kagame's extensive C.I.A. training, much less any U.S. complicity.[660].
Also missing from the official MSM narrative is the sworn testimony before Congress (May 2001) and in France (2002) by NSA military intelligence analyst Wayne Madsen who testified: "A French military intelligence officer said he detected some 100 armed U.S. troops in the eastern Zaire conflict zone," Madsen's statement began: "Moreover, the DGSE [French secret service] reported the Americans had knowledge of the extermination of Hutu refugees by Tutsis in both Rwanda and eastern Zaire and were doing nothing about it. More ominously, there was reason to believe that some U.S. forces, either Special Forces or mercenaries, may have actually participated in the extermination of Hutu refugees." (pp. 9-10).
[658]
H. Hrg. 107-16. (May 17, 2001). Testimony of Wayne Madsen. Genocide and Covert Operations in Africa 1993-1999. Subcommittee on International Operations and Human Rights, US 107th Congress, 1st Session. Serial No. 107-16. US House of Representatives.[662]
Wayne Madsen. (1999). Genocide and Covert Operations in Africa, 1993-1999. Mellen Press.
Guillaume Kress. (Sep. 09, 2015). Who Is Behind the Rwandan Genocide? Debunking the "Hutu Extremist" Myth. Global Research.[657]
Keith Harmon Snow. (Apr. 05, 2012). Pentagon Produces Satellite Photos Of 1994 Rwanda Genocide. Conscious Being.[658]
The official UN-sanctioned and amazingly unquestioned "Hutu genocide rampage" narrative is not credible just on the numbers, as proven by Global Research and common sense.

Rwandan Graveyard of Martyrs of the 100-day Globalist New World Order Atrocities of 1994. Lord have mercy. Photo: Unknown.
Rwandans martyred by Bill & Hillary Clinton & the Globalists

Skulls and bones of some of those killed in Rwanda's 100-day Globalist New World Order Atrocities are seen at a memorial shrine at a Catholic church in Ntarama, Rwanda, April 4, 2014. Lord have mercy.

The beneficiaries from the death and martyrdom of 1 million Rwandans were globalist technology companies who were securing their access to rare earth minerals needed in the manufacture of electronic devices. These minerals are plentiful in the mines of Central Africa. These natural resources should bring great wealth to the Central African economies, but do not because they are extracted under contracts with corrupt, globalist-backed New World Order dictators and strongmen.
These companies are members of:
(1) C.I.A.'s In-Q-Tel private venture capital company, (2) National Infrastructure Assurance/Advisory Council (NIAC), (3) the National Venture Capital Association (NCVA), (4) The IBM Eclipse Foundation, (5) Obama's Technology CEO's Council, and (6) Obama Silicon Valley outpost of the U.S. Digital Service funded with $1.5 billion in funds from Google's Eric E. Schmidt ... among others. Graphic: AFI.

Hillary R. Clinton

William J. Clinton
President Bill Clinton did nothing to stop this 100-day so-called "Rwandan Geno










 On Feb. 26, 1993, The 1993 World Trade Center bombing was alleged to be a terrorist attack on the World Trade Center. A truck bomb detonated below the North Tower of the World Trade Center in New York City. The 1,336 pounds (606 kg) urea nitrate–hydrogen gas enhanced device (supplied by an FBI Informant, see below) was intended, according to the official propaganda narrative, to send the North Tower (Tower 1) crashing into the South Tower (Tower 2), bringing both towers down and killing tens of thousands of people. It failed to do so, but killed six people and injured over a thousand.
On Feb. 26, 1993, The 1993 World Trade Center bombing was alleged to be a terrorist attack on the World Trade Center. A truck bomb detonated below the North Tower of the World Trade Center in New York City. The 1,336 pounds (606 kg) urea nitrate–hydrogen gas enhanced device (supplied by an FBI Informant, see below) was intended, according to the official propaganda narrative, to send the North Tower (Tower 1) crashing into the South Tower (Tower 2), bringing both towers down and killing tens of thousands of people. It failed to do so, but killed six people and injured over a thousand. Bill Clinton made fascist crony capitalism his policy, led by the White House with the C.I.A., NSA, State, Justice and Defense Departments
Bill Clinton made fascist crony capitalism his policy, led by the White House with the C.I.A., NSA, State, Justice and Defense Departments

